Consider this scenario: you’re sitting at your computer, minding your own business, and out of the blue, a message pops up on your screen demanding money or your personal information will be released to the public. You have no idea where the news came from or how it got onto your computer. This is a cyber threat—a real danger lurking online that can put your privacy and security at risk. Cyber threat intelligence (CTI) is a way to mitigate the risks by identifying and analyzing threats to help protect organizations from attack. So, what is CTI, and why do you need it? Read on to find out!
What is threat intelligence? Definition and explanation
Threat intelligence (TI) is data used to understand and anticipate cyber threats. This information can be gathered from various sources, including malware analysis, dark web monitoring, and phishing analysis. Once collected, this data is typically analyzed by security experts to identify patterns and trends. This helps improve cybersecurity defenses by allowing organizations to anticipate and defend against future attacks. To be effective, TI must be constantly updated and carefully reviewed. Additionally, it is essential to clearly understand how to interpret the data to avoid making inaccurate assumptions. When used correctly, however, threat intelligence can be a powerful tool for improving an organization’s security posture.
Threat intelligence (TI) is “evidence-based knowledge, including context, mechanisms, indicators, and warnings about an existing or imminent adversary or threat to support decision making regarding response options.”
Who benefits from Threat Intelligence?
Who benefits from threat intelligence? The answer may depend on your question, but some general principles can be applied.
- First, Indicators of compromise (IOCs) can be used to identify potential threats and investigate incidents.
- Second, threat intelligence feeds can provide real-time information about emerging threats.
- And finally, threat intelligence can help organizations to understand the risks they face and make informed decisions about how to respond.
Organizations that are particularly reliant on threat intelligence include:
- Cybersecurity teams, who use IOCs to identify and investigate potential incidents
- Incident response teams, use threat intelligence to understand and respond to incidents more effectively
- Security operations center (SOC) analysts, who use threat intelligence to detect and defend against threats
- Business continuity and disaster recovery teams*, who use threat intelligence to plan for and respond to disruptions
- Risk management teams use threat intelligence to identify and assess risks to the organization.
Ultimately, anyone who needs to understand and protect against threats can benefit from threat intelligence. By understanding the types of threats they face, organizations can make more informed decisions about allocating their resources and prioritizing their efforts.
Three types of threat intelligence
Cyber threat intelligence (CTI) refers to the evidence-based knowledge regarding an existing or imminent threat posed by an adversary or adversaries to organizational assets, including information systems, data, and networks. This understanding can help inform cybersecurity decision-making and strategy at the corporate level.
There are three primary types of cyber threat intelligence: strategic, operational, and tactical.
Strategic threat intelligence
is broad in scope and focuses on an organization’s long-term goal of identifying potential cyber threats that could impact its business objectives. Senior executives and Board members typically use it to make decisions about allocating resources and managing risk.
Operational threat intelligence
is more narrow in focus and is designed to help organizations defend against specific threats actively targeting their systems. It is typically used by front-line defenders, such as security analysts and incident responders, to identify and thwart attacks quickly.
Tactical threat intelligence
is the most specific type of CTI used to support short-term decision-making related to a particular incident or set of happenings? For example, it might be used to determine the origin of an attack or understand the methods and tools used so that steps can be taken to prevent future episodes.
Why is Threat Intelligence Important?
Threat intelligence has been defined in many ways. Still, the SANS Institute defines it as “actionable information that includes context, indicators, and mitigation strategies about an existing or impending cyber threat.” The intelligence must be timely, accurate, and relevant to your organization to be actionable. It is important to note that threat intelligence is different from security intelligence. Security intelligence focuses on internal events and threats, while threat intelligence focuses on external events and threats.
Organizations need to define an actionable threat and how it pertains to their business. Cybersecurity professionals need to be able to communicate the value of intelligence by tying it to organizational objectives. It is not enough to have data, but rather data that has been processed and analyzed in a way that provides context and understanding.
Actionable intelligence helps an organization understand:
-The who (attacker),
-What (techniques, tools, and procedures),
-When (timing of the attack),
-Where (geography),
-How (methodology used in the attack)
*nd why (motive behind the attack).
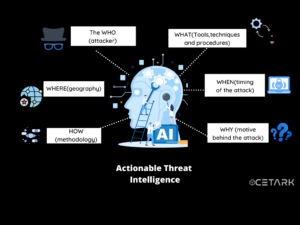
This information helps organizations develop plans and strategies to prevent, detect, and respond to attacks.
Threat intelligence is crucial because it:
– It helps reduce noise so analysts can focus on more critical threats
– Increases the speed of identifying and responding to incidents
– Improves accuracy in identifying potential attacks
– Enables better collaboration between security teams
– It helps organizations make more informed decisions about where to allocate resources.
What are some best practices for using threat intelligence?
Like all forms of intelligence, threat intelligence must be tailored to the organization’s specific needs. However, some best practices can be followed to make the most effective use of threat intelligence.
First, it is essential to have a clear understanding of the threat landscape. What types of threats are you most likely to face? What are their motivations? What methods do they typically use? This information will help you to prioritize the threat intelligence that you collect.
Second, it is essential to establish clear goals and objectives for your threat intelligence program. What information do you need to protect your organization? How will you use this information? By clearly defining your goals, you will be able to more effectively evaluate the usefulness of the threat intelligence that you collect.
Finally, it is essential to establish strong internal communication channels. Threat intelligence is only practical if it is shared with those who need it promptly. By setting clear protocols for disseminating threat intelligence throughout your organization, you can help to ensure that everyone is aware of the latest threats and knows how to best protect against them.
How does the Threat Intelligence platform work?
Threat Intelligence platforms are tools to collect and aggregate Threat Intelligence data in many formats from dozens or even thousands of internal and external sources. TIPs allow organizations to gather information about known threats, enabling effective and accurate identification of threats and their actions.
To work correctly, TIPs must constantly update the latest information on threats. This can be a challenge, as new threats are continually emerging. However, by using a TIP, organizations can stay ahead of the curve and protect themselves from the most up-to-date threats.
When used correctly, Threat Intelligence platforms can be an invaluable tool in the fight against cybercrime. Organizations can make better decisions about protecting their networks and data by staying informed about known threats. In addition, TIPs can help organizations respond quickly and effectively to new/emergent threats.
If you’re considering implementing a Threat Intelligence platform in your organization, you should keep a few things in mind. First, it’s essential to choose a platform that is right for your organization. There are many different TIPs on the market, so selecting one that will meet your specific needs is essential.
Second, you’ll need to ensure that your selected platform is compatible with your existing security infrastructure. If you have a current security solution in place, you’ll want to ensure that the Threat Intelligence platform you select can integrate seamlessly. Otherwise, you may end up with two separate systems that don’t work together correctly.
Finally, you’ll need to ensure that the Threat Intelligence platform you select offers the features and functionality you need. Some platforms offer more comprehensive threat intelligence than others. You’ll want to consider your organization’s specific needs when selecting a platform to get the most out of it.
When choosing a Threat Intelligence platform, there is no one-size-fits-all solution. However, by keeping these factors in mind, you can be sure to select a forum that will meet your organization’s specific needs. By doing so, you’ll be able to reap all the benefits that Threat Intelligence has to offer.
Threat Intelligence Lifecycle
 The threat intelligence lifecycle is the process analysts use to collect, analyze, and act on information about cybersecurity threats. It consists of four main phases:
The threat intelligence lifecycle is the process analysts use to collect, analyze, and act on information about cybersecurity threats. It consists of four main phases:
– Collection: In this phase, analysts gather data from internal and external sources. This data can come from news articles, blog posts, social media activity, malware samples, etc.
– Analysis: Once the data has been collected, it needs to be analyzed to extract useful information about potential threats. This typically includes identifying patterns and trends and understanding the motives and capabilities of specific threat actors.
– Dissemination: After the analysis is complete, the results need to be shared with decision-makers to take appropriate action. This phase also includes developing mitigation and response plans in case of an attack.
– Monitoring: Even after the initial threat has been dealt with; it’s essential to continue monitoring for new activity. This helps ensure that potential follow-up attacks are detected and dealt with quickly.
A threat intelligence lifecycle is essential for analysts who want to stay ahead of the latest cybersecurity threats. Following this process, they can collect and analyze data to identify trends and develop plans to protect their organizations from attacks.
Threat intelligence has become increasingly important in recent years as the number and sophistication of cyber threats have grown. It’s no longer enough to react to attacks after they happen—organizations need to be proactive to stay ahead of the curve.
Cyber threat intelligence can help organizations provide them with actionable information about potential threats. By understanding the latest trends and identifying the motives and capabilities of specific threat actors, organizations can develop better defenses and be prepared to respond quickly in the event of an attack.
What are some of the challenges with threat intelligence?
One of the biggest challenges with threat intelligence is getting accurate and timely information. This can be difficult because there are many different sources of information, and it can be hard to know which ones to trust. Another challenge is making sure that the information you have is actionable. This means that it should be relevant to your organization and help you decide how to protect your business. Finally, another challenge is staying up-to-date with the latest threats. This can be difficult because new threats are constantly emerging, and it can be hard to keep up with the changes.
Despite these challenges, threat intelligence is critical to any security strategy. By understanding the latest threats and having accurate information about them, you can make better decisions about how to protect your business.
Conclusion:
The key is to remember that cyber threat intelligence is not a one-size-fits-all solution. The type of intelligence you need will depend on your specific needs and goals.
If you’re still not sure whether or not you need CTI, ask yourself the following questions:
-Do I understand the threats my organization faces?
-Am I able to respond quickly and effectively to incidents?
-Do I have visibility into what is happening in my environment?
-Do I know where to allocate my resources to protect my organization?
-Am I prepared for future challenges?
If you answered “no” to any of these questions, then CTI can help.
Contact us today to learn more about how we can help you protect your business.